Which log type would provide information about traffic blocked by a Zone Protection profile?
A. Data Filtering
B. IP-Tag
C. Traffic
D. Threat
Explanation:
The question asks which log type would provide information about traffic blocked by a Zone Protection profile on a Palo Alto Networks firewall. A Zone Protection profile is a security feature that protects a zone from various threats, such as floods (e.g., SYN, ICMP), reconnaissance, and packet-based attacks, by defining thresholds and actions (e.g., block, alert). The log type must reflect the security events triggered by these protective actions. Let’s evaluate the options to determine the correct log type.
Why D. Threat?
Purpose: The Threat log (available under Monitor > Logs > Threat) records security events, including traffic blocked or alerted on by security features like Zone Protection profiles, Antivirus, Anti-Spyware, and Vulnerability Protection. When a Zone Protection profile blocks traffic (e.g., due to exceeding a SYN flood threshold), the event is logged as a threat with details such as the source/destination, action (block), and rule name.
Details in Log:
Type: Zone Protection (e.g., "flood" or "reconnaissance").
Action: Block, Alert, or Drop.
Source/Destination: IPs and zones involved.
Rule: The Zone Protection profile name.
Configuration:Enable logging in the Zone Protection profile under Network > Network Profiles > Zone Protection > Flood Protection or Reconnaissance Protection, setting the action to "Block" with logging enabled.
Behavior: The firewall logs the block action in the Threat log when the profile’s thresholds are exceeded, providing visibility into protected traffic.
Reference: Palo Alto Networks documentation states, "Zone Protection profile actions, such as blocking flood traffic, are logged in the Threat log."
Why Not the Other Options?
A. Data Filtering:
Explanation: The Data Filtering log (under Monitor > Logs > Data Filtering) records events related to data loss prevention (DLP) policies, such as file transfers or sensitive data detection. It is unrelated to Zone Protection profiles, which focus on network-layer threats, not content filtering.
Why Incorrect: This log type is for DLP, not zone protection.
B. IP-Tag:
Explanation: The IP-Tag log (under Monitor > Logs > IP-Tag) tracks the assignment and expiration of IP-to-User or IP-to-Device mappings by User-ID. It is used for identity-based policies, not for logging traffic blocked by Zone Protection profiles.
Why Incorrect: This is for User-ID tracking, not security blocks.
C. Traffic:
Explanation:The Traffic log (under Monitor > Logs > Traffic) records all allowed and denied traffic flows based on Security policies, including source, destination, application, and action (allow/deny). However, blocks due to Zone Protection profiles (e.g., SYN floods) are logged as threats, not traffic, because they are security events triggered by a protection mechanism, not a policy-based deny rule
Why Incorrect:
Traffic logs capture policy-based denials, not Zone Protection blocks.
Additional Context:
Zone Protection Profile: Configured under Network > Network Profiles > Zone Protection, it includes settings for flood protection (e.g., SYN, UDP), reconnaissance protection, and packet-based attack protection. Blocking actions generate threat logs.
Log Verification:
Check the Zone Protection profile settings for logging.
Review Monitor > Logs > Threat and filter by "Zone Protection" or "flood".
Use CLI command > show log threat to confirm.
Best Practices:
Set appropriate thresholds to avoid false positives.
Enable alerts for monitoring.
Correlate with Traffic logs for context.
PCNSE Exam Relevance: This question tests your understanding of log types and Zone Protection features, a key topic in the PCNSE exam. It requires knowledge of where security events are logged.
Conclusion:
The log type that provides information about traffic blocked by a Zone Protection profile is the Threat log, as it records security events triggered by the profile’s protective actions.
References:
Palo Alto Networks Documentation: Zone Protection Profiles
Palo Alto Networks Documentation: Threat Log Details
ExamTopics PCNSE Discussion: Zone Protection Logging
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
A. A self-signed Certificate Authority certificate generated by the firewall
B. A Machine Certificate for the firewall signed by the organization's PKI
C. A web server certificate signed by the organization's PKI
D. A subordinate Certificate Authority certificate signed by the organization's PKI
Explanation:
Why a Subordinate CA Certificate?
1.SSL Forward Proxy Trust Model:
The firewall acts as a man-in-the-middle (MITM) for HTTPS traffic.
It generates dynamic certificates for websites visited by users.
These dynamic certificates must be signed by a Certificate Authority (CA) that is trusted by all clients.
2.Benefits of a Subordinate CA:
Signed by the organization's root PKI: Already trusted by all domain-joined clients.
Delegated authority: Allows the firewall to issue certificates without involving the root CA.
Security best practice: Limits exposure of the root CA.
Why Not Other Options?
A. Self-signed CA
Not inherently trusted by clients—requires manual installation on every device.
B. Machine Certificate
Used for firewall identity (e.g., management), not signing dynamic certificates.
C. Web Server Certificate
Issued to servers, not for signing other certificates.
Deployment Steps:
Generate a subordinate CA certificate from the organization’s PKI.
Import it on the firewall under Device > Certificate Management > Certificates.
Reference it in the Decryption Profile (Forward Trust Certificate).
Reference:
Palo Alto Decryption Best Practices:
"Use a subordinate CA from your enterprise PKI as the forward trust certificate for seamless client trust."
An administrator is assisting a security engineering team with a decryption rollout for inbound and forward proxy traffic. Incorrect firewall sizing is preventing the team from decrypting all of the traffic they want to decrypt. Which three items should be prioritized for decryption? (Choose three.)
A. Financial, health, and government traffic categories
B. Known traffic categories
C. Known malicious IP space
D. Public-facing servers,
E. Less-trusted internal IP subnets
Explanation:
When firewall sizing limits the ability to decrypt all traffic, Palo Alto Networks recommends a staged and prioritized decryption rollout. The goal is to maximize security impact while minimizing resource consumption. The following traffic types should be prioritized:
A. Financial, health, and government traffic categories
✔️ These categories are high-value targets for data exfiltration and fraud. Decrypting them helps detect:
Malware hidden in encrypted sessions
Unauthorized data transfers
Compliance violations
C. Known malicious IP space
✔️ Decrypting traffic to/from known bad IPs allows:
Full inspection of payloads
Detection of command-and-control (C2) activity
Prevention of encrypted malware delivery
E. Less-trusted internal IP subnets
✔️ Internal segments that are not fully trusted (e.g., guest networks, unmanaged devices) should be decrypted to:
Detect lateral movement
Prevent insider threats
Enforce granular security policies
❌ Incorrect Options:
B. Known traffic categories
✖️ These are typically low-risk or well-understood applications (e.g., Microsoft updates, Zoom) and may not need decryption.
D. Public-facing servers
✖️ These are typically handled via SSL Inbound Inspection, not Forward Proxy, and are not bulk user traffic.
Authoritative Source:
Palo Alto Networks – Size the Decryption Firewall Deployment
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user. What configuration change is necessary to implement this troubleshooting solution for the user?
A. Enable SSL tunnel within the GlobalProtect gateway remote user's settings.
B. Modify the user's client to prioritize UDP traffic for GlobalProtect.
C. Enable SSL tunnel over TCP in a new agent configuration for the specific user.
D. Increase the user's VPN bandwidth allocation in the GlobalProtect settings.
Explanation:
Why This Option?
1.Problem:
Intermittent connectivity due to UDP packet loss (as seen in packet captures).
Solution: Force the user’s GlobalProtect client to use TCP instead of UDP for reliability.
2.Configuration:
Create a new Agent Configuration (under Network > GlobalProtect > Agent Settings) with:
Tunnel Mode = SSL (which uses TCP port 443).
Assign this configuration to the specific user via User/Group ID or Source IP.
Why Not Other Options?
A.GlobalProtect gateways don’t have per-user SSL tunnel settings—this is configured in agent settings.
B.Prioritizing UDP would worsen the packet loss issue.
D.Bandwidth allocation doesn’t fix packet loss; it only manages throughput.
Steps:
Navigate to: Network > GlobalProtect > Agent Settings > Add.
Set Tunnel Protocol = SSL (forces TCP).
Scope to the user via Source User or Source IP.
Reference:
GlobalProtect Admin Guide:
"Use Agent Configurations to enforce TCP-based SSL tunnels for users experiencing UDP issues."
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
A. Set the passive link state to shutdown".
B. Disable config sync.
C. Disable the HA2 link.
D. Disable HA.
Explanation:
Why Disable Config Sync?
1.HA Pair Behavior:
In an active/passive HA pair, the active firewall handles traffic while the passive firewall syncs configuration and sessions.
When you import the HA pair into Panorama, Panorama pushes configurations to both firewalls.
2.Risk of Disruption:
If the configuration push occurs during sync, it may cause temporary inconsistencies or restart services (e.g., routing daemons).
Disabling config sync temporarily prevents the passive firewall from receiving changes, avoiding disruptions.
3.Safe Import Steps:
Disable config sync on the HA pair:
> set high-availability state-synchronization enabled no
Import the configuration into Panorama.
Re-enable config sync after import.
Why Not Other Options?
A.Shutting down the passive link breaks HA integrity (may trigger failover).
C.Disabling HA2 breaks session sync (causes session loss on failover).
D.Disabling HA entirely breaks redundancy and may disrupt traffic.
Reference:
Panorama HA Integration Guide:
"Temporarily disable state synchronization before importing HA configurations to avoid traffic impact."
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices. What should an administrator configure to route interesting traffic through the VPN tunnel?
A. Proxy IDs
B. GRE Encapsulation
C. Tunnel Monitor
D. ToS Header
Explanation:
Why Proxy IDs?
1.Policy-Based VPNs:
For policy-based VPNs (common with third-party devices), Proxy IDs define the "interesting traffic" that should be routed through the tunnel.
They specify the source and destination subnets (and sometimes protocols/ports) that trigger encryption.
2.Configuration:
On the Palo Alto firewall, Proxy IDs are set under:
Network > IPsec Tunnels > [Tunnel] > Proxy IDs.
Must match exactly on both ends of the VPN.
Why Not Other Options?
B. GRE Encapsulation
Used for GRE tunnels, not IPsec policy-based VPNs.
C. Tunnel Monitor
Checks tunnel liveliness (doesn’t define traffic).
D. ToS Header
Used for QoS, not traffic selection.
Reference:
Palo Alto IPsec VPN Guide:
"Proxy IDs determine which traffic is encrypted in policy-based VPNs."
Which source is the most reliable for collecting User-ID user mapping?
A. Syslog Listener
B. Microsoft Exchange
C. Microsoft Active Directory
D. GlobalProtect
Explanation:
Microsoft Active Directory (AD) is the most reliable source for collecting User-ID user mapping because it serves as the central authentication system in most enterprises, providing real-time, accurate IP-to-user mappings via security event logs (e.g., Event ID 4624) through the User-ID agent. Its scalability and comprehensive coverage of domain-joined devices make it ideal.
A. Syslog Listener:
Less reliable as it depends on external devices’ logging consistency, which can be inconsistent or incomplete.
B. Microsoft Exchange:
Limited to email-related events, making it narrow and less reliable for full user mapping.
C. Microsoft Active Directory:
As explained, the most reliable due to its authoritative and real-time data.
D. GlobalProtect:
Reliable for VPN users but incomplete, as it only covers GlobalProtect clients, not all internal users.
References:
Palo Alto Networks Documentation: User-ID with Active Directory
Palo Alto Networks Documentation: User Mapping Sources
ExamTopics PCNSE Discussion: User-ID Reliability
Refer to the exhibit.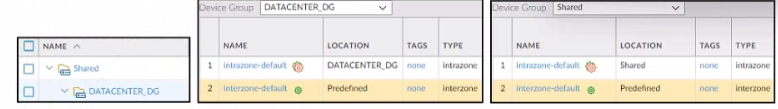
Based on the screenshots above what is the correct order in which the various rules are
deployed to firewalls inside the DATACENTER_DG device group?
A. shared pre-rules
DATACENTER DG pre rules
rules configured locally on the firewall
shared post-rules
DATACENTER_DG post-rules
DATACENTER.DG default rules
B. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
shared post-rules
DATACENTER.DG post-rules
shared default rules
C. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
DATACENTER_DG post-rules
shared post-rules
shared default rules
D. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
DATACENTER_DG post-rules
shared post-rules
DATACENTER_DG default rules
Explanation:
When Panorama pushes policies to firewalls in a device group like DATACENTER_DG, the rules are evaluated in a strict order to ensure consistent policy enforcement. The correct deployment order is:
Shared pre-rules – Global rules pushed to all firewalls
DATACENTER_DG pre-rules – Device-group-specific rules applied before local rules
Local firewall rules – Rules configured directly on the firewall
Shared post-rules – Global rules applied after local rules
DATACENTER_DG post-rules – Device-group-specific rules applied after shared post-rules
Shared default rules – Predefined rules like intrazone-default and interzone-default
This order ensures that organization-wide policies are enforced first, followed by device-specific logic, and finally default behavior.
📘 Authoritative Source:
Panorama Device Group Policies – Palo Alto TechDocs
| Page 9 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home | Previous |