An administrator is using Panorama to manage multiple firewalls. After upgrading all
devices to the latest PAN-OS software, the administrator enables log forwarding from the
firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to
Panorama?
A. Export the log database.
B. Use the import option to pull logs.
C. Use the scp logdb export command.
D. Use the ACC to consolidate the logs.
Explanation:
When you configure log forwarding from firewalls to Panorama, only new logs generated after enabling the feature are forwarded.
Pre-existing logs already stored on the local firewall’s log database will not be automatically sent to Panorama.
To move old logs, you need to manually export them from the firewall log database and import them into Panorama
.
The correct method is to run the scp logdb export command on the firewall, which securely copies the firewall’s log database to Panorama (or another SCP server for import).
Why not the others?
A. Export the log database
→ too vague; doesn’t specify the actual mechanism (SCP is required).
B. Use the import option to pull logs
→ Panorama cannot pull logs from firewalls; logs must be pushed/exported.
D. Use the ACC to consolidate the logs
→ ACC (Application Command Center) only summarizes existing logs; it cannot retrieve old logs from firewalls.
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A. Traffic logs
B. Data filtering logs
C. Policy Optimizer
D. Wireshark
Explanation:
The scenario involves a firewall engineer tasked with defining signatures for a custom application on a Palo Alto Networks firewall. Custom application signatures are created using the Application Override or Custom Application features in PAN-OS to identify unique traffic patterns. The engineer needs sources to gather information about the application’s patterns (e.g., ports, protocols, packet contents). Let’s evaluate the options to determine the two appropriate sources.
Why A. Traffic logs?
Purpose: Traffic logs (available under Monitor > Logs > Traffic) record details of network traffic processed by the firewall, including source/destination IPs, ports, protocols, and application identification attempts. For a custom application not yet recognized by App-ID, the logs can show the traffic’s behavior (e.g., consistent use of a non-standard port like TCP 12345) and help identify patterns that can be used to define a signature.
Use Case: The engineer can filter logs for traffic from known clients or servers of the custom application, noting the port, protocol, and any identifiable payload characteristics to inform the signature.
Reference:
Palo Alto Networks documentation suggests, "Traffic logs can be analyzed to identify patterns for custom application signatures."
Why D. Wireshark?
Purpose:
Wireshark is a packet analysis tool that captures and inspects network traffic in real-time, providing detailed packet-level information (e.g., headers, payloads, protocol sequences). The engineer can use Wireshark to capture traffic from the custom application, analyzing its unique patterns (e.g., specific byte sequences, handshake behavior) to create an accurate custom signature.
Use Case: By setting up a capture on the network segment where the application operates, the engineer can extract protocol details and payload data to define match conditions in the firewall’s custom application settings.
Reference:
Palo Alto Networks documentation recommends, "Packet captures from tools like Wireshark can be used to gather detailed traffic patterns for custom application signatures."
Why Not the Other Options?
B. Data filtering logs:
Explanation: Data filtering logs (under Monitor > Logs > Data Filtering) record events related to data loss prevention (DLP) or file transfer policies, focusing on file types and content rather than application identification patterns. These logs are not designed to provide the protocol or traffic behavior data needed to define a custom application signature.
Why Incorrect: These logs are irrelevant to application pattern analysis.
C. Policy Optimizer:
Explanation: The Policy Optimizer (under Policies > Policy Optimizer) analyzes traffic logs to identify unused or shadowed Security rules and suggests optimizations. While it uses traffic data, it is a post-analysis tool for policy refinement, not a source for gathering raw application pattern information to create signatures.
Why Incorrect: This is for policy optimization, not signature development.
Additional Context:
Custom Application Signatures: Defined under Objects > Custom Objects > Applications, these signatures use pattern matching (e.g., port, protocol, regular expressions) to identify custom apps. Sources like traffic logs and packet captures provide the necessary data.
Configuration Steps:
Analyze Traffic logs for port/protocol usage.
Use Wireshark to capture and decode packets.
Create a custom application with the identified patterns (e.g., port 12345, TCP, specific string).
Test the signature with Monitor > Packet Capture.
Best Practices:
Capture traffic during peak usage for accuracy.
Validate signatures with test traffic.
Update signatures if the application behavior changes.
PCNSE Exam Relevance:
This question tests your understanding of custom application signature creation, a key topic in the PCNSE exam. It requires knowledge of data sources for pattern analysis.
Conclusion:
The two sources the engineer can use to gather information about the custom application’s patterns are Traffic logs for high-level traffic behavior and Wireshark for detailed packet-level analysis, enabling the creation of effective signatures.
References:
Palo Alto Networks Documentation: Custom Application Signatures
Palo Alto Networks Documentation: Traffic Log Analysis
ExamTopics PCNSE Discussion: Custom App Signature Sources
Which two scripting file types require direct upload to the Advanced WildFire portal/API for analysis? (Choose two.)
A. Ps1
B. Perl
C. Python
D. VBS
Explanation:
Why These File Types?
PowerShell (.ps1) and VBScript (.vbs) are scripting languages commonly used in malware.
The Advanced WildFire portal/API requires direct upload for these because:
They are not executable binaries (e.g., .exe, .dll) that can be analyzed via standard WildFire submission (e.g., email, URL).
They require specialized sandboxing to simulate execution and detect malicious behavior.
Why Not Others?
Perl (.pl) and Python (.py) can also be analyzed, but they are less commonly targeted for direct upload requirements in this context. However, the question specifies "require direct upload," and PowerShell and VBScript are the most critical due to their prevalence in attacks.
Reference:
Palo Alto WildFire Admin Guide:
"Script files (e.g., .ps1, .vbs) must be uploaded directly to the Advanced WildFire portal for analysis."
<
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
A. OSPFV3
B. ECMP
C. ASBR
D. OSBF
Explanation:
Why OSPFv3?
1.Multiple OSPF Instances over a Single Link:
OSPFv3 (Open Shortest Path First version 3) supports multiple instances on a single interface.
Each instance operates independently, allowing different routing domains (areas) to share the same physical link.
2.Key Feature:
OSPFv3 uses Instance ID (ranging from 0 to 255) to differentiate between instances on the same link.
This enables segregation of routing information (e.g., limiting route sharing between areas).
Why Not Other Options?
B. ECMP
Equal-Cost Multi-Pathing balances traffic across multiple routes, but doesn’t support multiple OSPF instances.
C. ASBR
Autonomous System Boundary Router connects OSPF to other protocols, but doesn’t enable multiple instances on a link.
D. OSBF
Not a valid protocol (likely typo for OSPF).
Configuration Example:
In the virtual router, configure OSPFv3 with distinct instance IDs for each area.
Reference:
Palo Alto OSPFv3 Documentation:
"OSPFv3 instance IDs allow multiple routing domains over a single link."
A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3. Which command should they use?
A. test routing route ip 10.2.5.3 *
B. test routing route ip 10.2.5.3 virtual-router default
C. test routing fib-lookup ip 10.2.5.0/24 virtual-router default
D. test routing fib-lookup ip 10.2.5.3 virtual-router default
Explanation:
Why This Command?
1.Purpose:
The command test routing fib-lookup checks the Forwarding Information Base (FIB) to determine the egress interface for a specific IP.
It simulates how the firewall will route the packet.
Syntax:
test routing fib-lookup ip
Example:
test routing fib-lookup ip 10.2.5.3 virtual-router default
Why Not Other Options?
A.Invalid syntax (missing virtual-router parameter).
B.test routing route is for checking route table, not FIB.
C.Uses a subnet (10.2.5.0/24) instead of the specific IP (10.2.5.3).
Key Difference:
FIB is the optimized forwarding table derived from the routing table.
fib-lookup gives the actual egress interface, while route shows route table matches.
Reference:
Palo Alto CLI Reference:
"Use test routing fib-lookup to determine the egress interface for a destination IP."
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
A. Configure the decryption profile
B. Define a Forward Trust Certificate
C. Configure SSL decryption rules
D. Configure a SSL/TLS service profile
Explanation:
To deploy SSL Forward Proxy decryption, an engineer must perform a series of steps. The two most fundamental are:
Define a Forward Trust Certificate (B):
The firewall must act as a trusted intermediary. To do this, it needs to have a Forward Trust Certificate, which is a Certificate Authority (CA) certificate that is trusted by the clients on the network. The firewall will use this certificate to sign the new, dynamically generated certificates it presents to the clients during the decryption process. Without this trusted CA, clients will receive certificate errors.
Configure SSL decryption rules (C):
After the certificate is in place, the engineer must create a decryption rule. This rule specifies which traffic to decrypt (e.g., all traffic, specific applications, specific URLs). The action of the rule is set to Decrypt, which tells the firewall to perform a man-in-the-middle decryption on the matching traffic.
The other options are important but are secondary to these two core actions:
A. Configure the decryption profile:
A decryption profile is an object that defines the details of the decryption process (e.g., protocols, ciphers, handling of untrusted certificates). It is an essential part of a best-practice decryption policy, but the policy itself (the rule) must be configured to use it.
D. Configure a SSL/TLS service profile:
This profile is used to secure the firewall's own management services, not to decrypt traffic passing through the firewall.
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
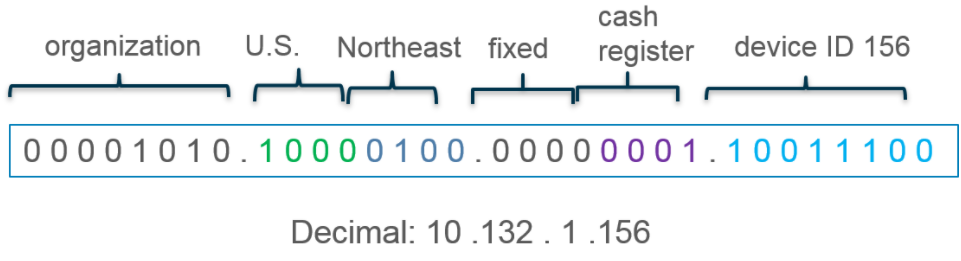
A. IP Netmask
B. IP Wildcard Mask
C. IP Address
D. IP Range
Explanation:
Why Wildcard Mask?
1.Address Structure with Meaningful Bits:
The diagram shows an IP address (10.132.1.156) where certain bits represent specific attributes (e.g., organization, region, device type).
To create an address object that matches devices based on these meaningful bits (ignoring others), a wildcard mask is ideal.
2.Wildcard Mask Flexibility:
Unlike a subnet mask (which matches contiguous bits), a wildcard mask allows selective matching of non-contiguous bits.
Example:
To match all devices in the "Northeast" region (regardless of other attributes), set wildcard bits to 0 for fixed bits and 1 for variable bits.
Why Not Other Options?
A. IP Netmask
Only matches contiguous networks (e.g., 10.132.1.0/24), not arbitrary bits.
C. IP Address
Matches a single IP, not a group.
D. IP Range
Matches a sequential range, not bit-based patterns.
Example Configuration:
To match all Northeast devices (assuming bits 8-15 represent region):
Address: 10.132.0.0
Wildcard Mask: 0.0.255.255 (ignore last two octets).
Reference:
Palo Alto Address Objects Guide:
"Wildcard masks enable matching based on arbitrary bit positions in IP addresses."
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
A. certificates
B. profiles
C. link state
D. stateful firewall connection
Explanation:
To establish a Palo Alto Networks firewall as a trusted third party for SSL/TLS decryption, the firewall must use certificates—specifically:
A Forward Trust Certificate:
Used to sign impersonated server certificates during SSL Forward Proxy. This certificate must:
Be a CA certificate
Include the private key
Be trusted by client devices (either self-signed and distributed, or signed by an enterprise CA)
A Forward Untrust Certificate:
Presented to clients when the firewall encounters a server certificate that is untrusted, ensuring users receive proper warnings.
These certificates allow the firewall to intercept, decrypt, inspect, and re-encrypt SSL/TLS traffic while maintaining trust between client and server.
📘 Authoritative Source:
Palo Alto Networks – Configure SSL Forward Proxy
| Page 8 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home | Previous |