Review the screenshots.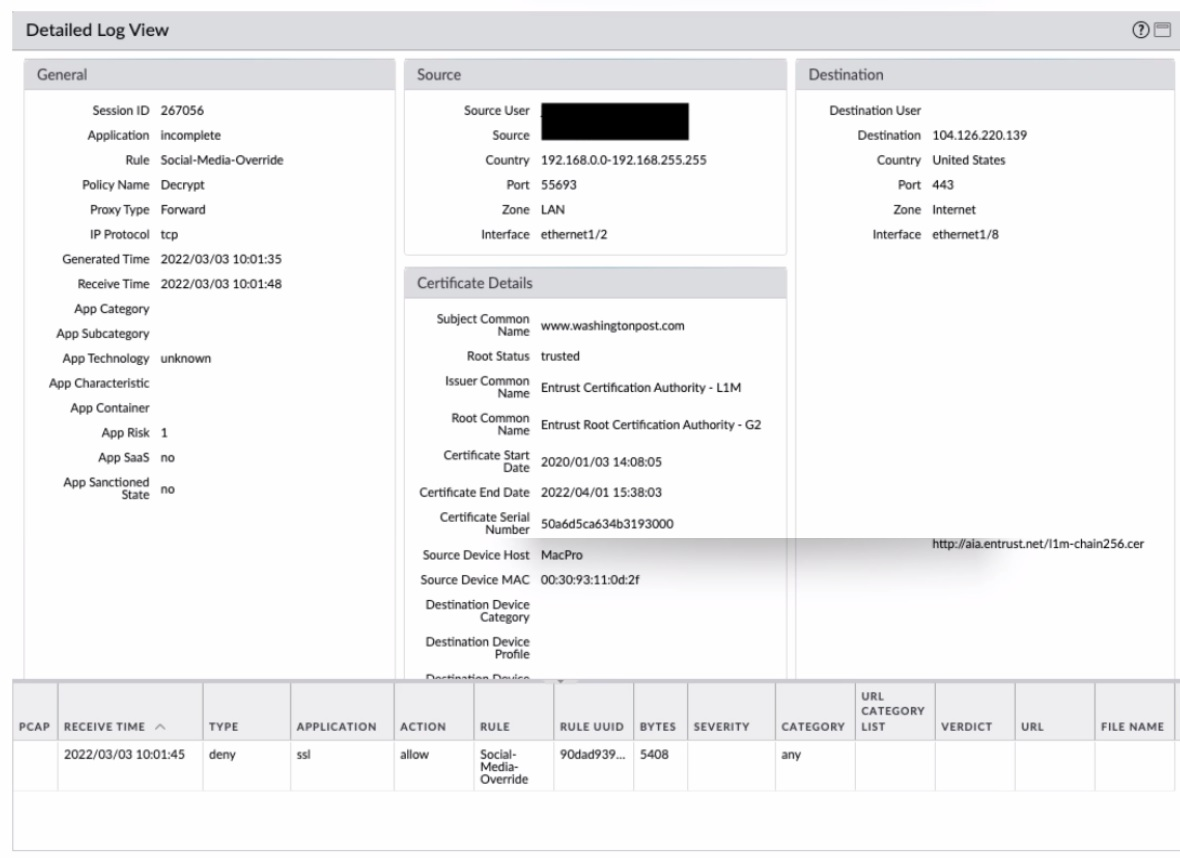
What is the most likely reason for this decryption error log?
A. The Certificate fingerprint could not be found.
B. The client expected a certificate from a different CA than the one provided.
C. The client received a CA certificate that has expired or is not valid.
D. Entrust is not a trusted root certificate authority (CA).
Explanation:
Key Evidence from the Log:
1.Certificate Details:
Issuer: Entrust Certification Authority - L1M
Root CA: Entrust Root Certification Authority - G2 (trusted).
Expiry Date: 2022/04/01 15:38:03 (log timestamp: 2022/03/03).
The certificate was still valid at the time of the session, but the log shows a deny action.
2.Error Context:
Action: deny (blocked by rule Social-Media-Override).
Application: ssl (TLS/SSL handshake failure).
3.Possible Causes:
Intermediate CA (L1M) expired/revoked: Though the root CA is trusted, the chain might be broken.
Certificate validation failure: The firewall or client rejected the intermediate CA.
Why Not Other Options?
ANo mention of fingerprint mismatch in the log.
BThe log confirms the expected CA (Entrust).
DEntrust is trusted (Root CA is listed as trusted).
Root Cause Analysis:
The intermediate CA (L1M) might have been:
Revoked (not shown in the log but plausible).
Expired post-log (though the log shows it was valid at the time).
The firewall’s decryption profile likely enforced strict validation, rejecting the chain.
Reference:
Palo Alto Decryption Troubleshooting:
"Denied SSL sessions often result from invalid intermediate CA certificates or revocation checks."
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama?
A. A User-ID Certificate profile must be configured on Panorama.
B. The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
C. User-ID Redistribution must be configured on Panorama to ensure that all firewalls have the same mappings.
D. A master device with Group Mapping configured must be set in the device group where the Security rules are configured.
Explanation:
To allow an administrator to select users and groups from Active Directory (AD) when building security rules in a Panorama Device Group, the Group Mapping configuration must be a part of a Master Device within that Device Group.
1.Master Device:
In a Panorama Device Group, a "Master Device" is the firewall that serves as the source of configuration for shared settings, including User-ID and Group Mapping. By designating a firewall as the master, Panorama pulls the user and group information that the firewall has learned from Active Directory.
2.Group Mapping:
This is the specific configuration that tells the Palo Alto Networks firewall how to connect to Active Directory (via LDAP) to pull user group information. The firewall queries AD and creates a mapping of users to their group memberships. This is the crucial step that makes AD groups available for use in security policies.
By making one of the firewalls a master device and ensuring it has a correctly configured Group Mapping, Panorama can then retrieve the user and group information from that device. This information becomes visible in Panorama's user and group selectors, allowing the administrator to build rules using AD groups for any firewall in that device group.
Why the other options are incorrect:
A. A User-ID Certificate profile must be configured on Panorama:
A certificate profile is used for authenticating with various services, but it is not the mechanism for pulling user and group mappings from a directory server. That is the job of Group Mapping.
B. The Security rules must be targeted to a firewall in the device group and have Group Mapping configured:
While Group Mapping must be configured, it is not configured on the security rules themselves. It is a separate configuration on the firewall, and its information is then made available to Panorama.
C. User-ID Redistribution must be configured on Panorama to ensure that all firewalls have the same mappings:
User-ID Redistribution is used to share user-to-IP address mappings among firewalls. This is different from Group Mapping, which is about mapping usernames to group memberships. While both are related to User-ID, Redistribution itself doesn't make the AD groups selectable in Panorama's rule-building interface.
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment. Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A. Kerberos or SAML authentication need to be configured
B. LDAP or TACACS+ authentication need to be configured
C. RADIUS is only supported for a transparent Web Proxy.
D. RADIUS is not supported for explicit or transparent Web Proxy
Explanation:
PAN-OS 11.0 explicit Web Proxy supports only Kerberos, SAML, and Cloud Identity Engine for authentication. RADIUS is not supported for either explicit or transparent proxy modes.
A. Kerberos or SAML authentication need to be configured
✔️ Correct — These are the supported methods for explicit proxy authentication in PAN-OS 11.0 Reference:
Palo Alto TechDocs – Configure Authentication for Explicit Web Proxy
D. RADIUS is not supported for explicit or transparent Web Proxy
✔️ Correct — RADIUS is not a supported authentication method for either proxy mode
❌ Incorrect Options:
B. LDAP or TACACS+ authentication need to be configured
❌ LDAP/TACACS+ are not supported for Web Proxy authentication in PAN-OS 11.0
C. RADIUS is only supported for a transparent Web Proxy
❌ Misleading — RADIUS is not supported for transparent proxy either
An engineer is configuring a firewall with three interfaces:
A. Set DNS and Palo Alto Networks Services to use the ethernet1/1 source interface.
B. Set DNS and Palo Alto Networks Services to use the ethernet1/2 source interface.
C. Set DNS and Palo Alto Networks Services to use the MGT source interface.
D. Set DDNS and Palo Alto Networks Services to use the MGT source interface.
Explanation:
Why This Option?
1.Service Route Configuration Purpose:
Determines which interface is used for outbound management traffic (e.g., DNS, updates, license checks).
By default, the MGT interface is used, but this can be overridden to use a data plane interface (e.g., ethernet1/1).
2.Key Requirements:
Dynamic updates (e.g., threat updates, PAN-DB URL filtering) require internet access.
The edge router-connected interface (ethernet1/1) is the logical choice for internet-bound traffic.
3.Configuration Steps:
Navigate to: Setup > Services > Service Route Configuration.
Set DNS and Palo Alto Networks Services to use ethernet1/1 as the source interface.
Why Not Other Options?
B (ethernet1/2)
Visualization network likely lacks internet access.
C/D (MGT)
Defeats the goal of using a data plane interface for updates.
D (DDNS)
Dynamic DNS is irrelevant for threat/update traffic.
Reference:
Palo Alto Admin Guide (Service Routes):
"Service routes allow dynamic updates to use data plane interfaces for internet access."
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing. What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
A. Add the Evernote application to the Security policy rule, then add a second Security policy rule containing both HTTP and SSL.
B. Create an Application Override using TCP ports 443 and 80.
C. Add the HTTP. SSL. and Evernote applications to the same Security policy
D. Add only the Evernote application to the Security policy rule.
Explanation:
Palo Alto Networks firewalls use App-ID, a patented technology that identifies applications regardless of the port, protocol, or encryption used. App-ID works by using multiple classification techniques, including application signatures, protocol decoding, and heuristics, to accurately identify the application running on the network.
When you add the Evernote application to a security policy, the firewall's App-ID engine takes care of identifying and allowing all the necessary components for that application to function correctly, including its implicit use of SSL and web browsing.
App-ID Dependency:
The firewall understands the dependencies of applications. For example, it knows that Evernote traffic includes both the core Evernote application traffic and the underlying SSL and web-browsing protocols that it uses to communicate.
Default Behavior:
By default, when you select a higher-level application like evernote, the firewall implicitly allows the dependent applications like ssl and web-browsing. You don't need to manually add them to the rule. Doing so would be redundant and could potentially open up your network to unwanted traffic from other applications that also use SSL and web-browsing.
Therefore, the minimum and most secure configuration is to add only the Evernote application to the security policy rule. The firewall's App-ID will handle the rest.
The other options are incorrect:
A & C: Adding separate rules or including http and ssl in the same rule would be redundant and less secure. It would allow any traffic using HTTP/SSL to pass through, not just Evernote.
B: Application Override is used to bypass App-ID's default behavior, typically for custom or non-standard applications. It's not the correct approach here, as the firewall already has a signature for Evernote.
References:
App-ID Overview, Create a Security Policy Rule
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1. In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
A. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: Static IP / 172.16.15.1
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 172.16.15.10 -
Application: ssh
B. NAT Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP / 172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
C. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP /172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
D. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: dynamic-ip-and-port / ethernet1/4
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
Explanation:
The SSH server is configured to only respond to requests from IP 172.16.16.1. To meet this requirement, the firewall must perform Source NAT so that outbound SSH traffic from the Trust zone appears to originate from that specific IP.
The correct configuration is:
1.NAT Rule:
Source Zone: Trust
Source IP: Any
Destination Zone: Server
Destination IP: 172.16.15.10
Source Translation: dynamic-ip-and-port / ethernet1/4
2.Security Rule:
Source Zone: Trust
Source IP: Any
Destination Zone: Server
Destination IP: 172.16.15.10
Application: ssh
3.This setup ensures:
Traffic from internal users is NATed to the expected source IP.
The SSH server receives traffic that matches its configured source filter.
The firewall allows the traffic through the correct zones and application.
📘 Reference:
Verified via Exam4Training PCNSE Question #71 and Ace4Sure PCNSE Scenario
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
A. No Direct Access to local networks
B. Tunnel mode
C. iPSec mode
D. Satellite mode
Explanation:
Why Tunnel Mode?
1.Split-Tunneling Granularity:
Tunnel mode is the only GlobalProtect gateway setting that supports split-tunneling by access route, destination domain, and application simultaneously.
It allows administrators to define:
Access Routes: Specific IP subnets to tunnel (e.g., corporate networks).
Domains: Destination domains (e.g., *.company.com) to tunnel.
Applications: Specific executables (e.g., outlook.exe) to tunnel.
2.How It Works:
Traffic matching any of these criteria is routed through the VPN tunnel.
Non-matching traffic (e.g., general web browsing) accesses the internet directly.
Why Not Other Options?
ADisables split-tunneling entirely (forces all traffic through VPN).
CIPSec mode is legacy and does not support domain/application-based split-tunneling.
DSatellite mode is for cloud gateways and lacks granular split-tunneling controls.
Configuration Steps:
Navigate to: Network > GlobalProtect > Gateways > [Gateway] > Agent > Split Tunnel.
Set Tunnel Mode = Enabled.
Configure:
Access Routes (e.g., 10.0.0.0/8).
Domains (e.g., *.internal.com).
Applications (e.g., ms-outlook.exe).
Reference:
Palo Alto GlobalProtect Admin Guide
"Tunnel mode enables advanced split-tunneling by access route, domain, and application."
An engineer is deploying multiple firewalls with common configuration in Panorama. What are two benefits of using nested device groups? (Choose two.)
A. Inherit settings from the Shared group
B. Inherit IPSec crypto profiles
C. Inherit all Security policy rules and objects
D. Inherit parent Security policy rules and objects
Explanation:
The scenario involves an engineer deploying multiple firewalls with a common configuration using Panorama, and the question asks for two benefits of using nested device groups. Nested device groups in Panorama allow for a hierarchical structure where settings and policies can be inherited from parent groups, providing flexibility and centralized management. Let’s evaluate the options to determine the correct benefits.
Why A. Inherit settings from the Shared group?
Purpose: In Panorama, the Shared group is a top-level container that holds configurations (e.g., network settings, templates, and objects) applicable to all device groups unless overridden. Nested device groups can inherit these settings, allowing the engineer to define common configurations (e.g., DNS, NTP, or interface settings) at the Shared level and apply them to all firewalls, reducing redundancy.
Benefit: This enables consistent baseline configurations across all firewalls while allowing nested groups to customize specific settings as needed. It simplifies management by centralizing common settings.
Reference:
Palo Alto Networks documentation states, "Nested device groups can inherit settings from the Shared group, providing a foundation for common configurations."
Why D. Inherit parent Security policy rules and objects?
Purpose: Nested device groups inherit Security policy rules and objects (e.g., addresses, services, applications) from their parent device groups. This hierarchical inheritance allows the engineer to define broad policies at a higher-level parent group (e.g., allowing HTTP traffic) and refine or add specific rules in lower-level nested groups (e.g., restricting HTTP to certain users), tailoring policies to specific firewall subsets.
Benefit: It promotes reusability and consistency across firewalls while enabling granular control. Changes at the parent level automatically propagate to nested groups unless overridden, streamlining policy management.
Reference:
Palo Alto Networks documentation notes, "Nested device groups inherit Security policy rules and objects from parent groups, allowing for layered policy design."
Why Not the Other Options?
B. Inherit IPSec crypto profiles:
Explanation: IPSec crypto profiles (e.g., encryption algorithms, authentication methods) are configured within network templates or template stacks, not device groups. Device groups handle policies (e.g., Security, NAT), while templates manage network and device settings (e.g., IPSec profiles). Nested device groups do not inherit IPSec crypto profiles directly; these are inherited via template stacks.
Why Incorrect:
This is a template-level setting, not a device group benefit.
C. Inherit all Security policy rules and objects:
Explanation: This option suggests inheritance from all levels (e.g., Shared and all parent groups), but nested device groups inherit only from their immediate parent group in the hierarchy, not all groups. They can also inherit from the Shared group independently. The inheritance is selective and hierarchical, not a blanket inheritance of all rules and objects.
Why Incorrect: This overstates the scope of inheritance; it’s limited to the parent group’s rules and objects.
Additional Context:
Nested Device Groups: These are organized in a parent-child hierarchy within Panorama. For example, a parent group might contain baseline Security rules, while a child group adds specific exceptions. The Shared group provides a global baseline.
Configuration Steps:
Navigate to Panorama > Device Groups.
Create a parent device group (e.g., "Global-Policies") and a nested group (e.g., "Regional-Policies").
Define common settings/rules in the Shared group and parent group, then refine in the nested group.
Push the configuration to the firewalls.
Best Practices:
Use nested groups to reflect organizational structure (e.g., regions, departments).
Minimize overrides to maintain consistency.
Test policy inheritance with Panorama > Preview Changes.
PCNSE Exam Relevance:
This question tests your understanding of Panorama’s device group hierarchy and inheritance, a key topic in the PCNSE exam. It requires knowledge of how nested groups enhance configuration management.
Conclusion:
Two benefits of using nested device groups are that they inherit settings from the Shared group (providing a common baseline) and inherit parent Security policy rules and objects (enabling layered policy design), improving efficiency and consistency across multiple firewalls.
References:
Palo Alto Networks Documentation: Panorama Device Groups and Inheritance
Palo Alto Networks Documentation: Nested Device Group Configuration
ExamTopics PCNSE Discussion: Panorama Nested Groups
| Page 5 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home | Previous |