Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
A. Log Ingestion
B. HTTP
C. Log Forwarding
D. LDAP
Explanation:
1. Recall how tag sharing works
Palo Alto firewalls can tag IPs based on log events (e.g., threat logs, traffic logs).
Those tags can be exported to a remote User-ID agent for consumption (for example, to populate Dynamic Address Groups).
To make this happen, you need two things:
A Log Forwarding profile to send the log entries.
An HTTP profile to define how logs are forwarded (via XML API to the User-ID agent).
2. Analyze the options
A. Log Ingestion
Not a configurable profile in PAN-OS. PAN-OS ingests logs, but this isn’t a profile type you configure.
❌
B. HTTP
✅ Yes. You need an HTTP Server Profile that defines how logs are sent (destination = User-ID agent or Cortex Data Lake, etc.).
C. Log Forwarding
✅ Yes. You attach a Log Forwarding Profile to the security rule or threat log, specifying that logs should be forwarded to the HTTP server.
D. LDAP
LDAP profiles are used for authentication and group mapping, not for sharing tags via logs.
❌
📖 Reference
Palo Alto Networks:
Forward Logs to an HTTP Destination
Palo Alto Networks:
Use Log Forwarding to Tag/Detag
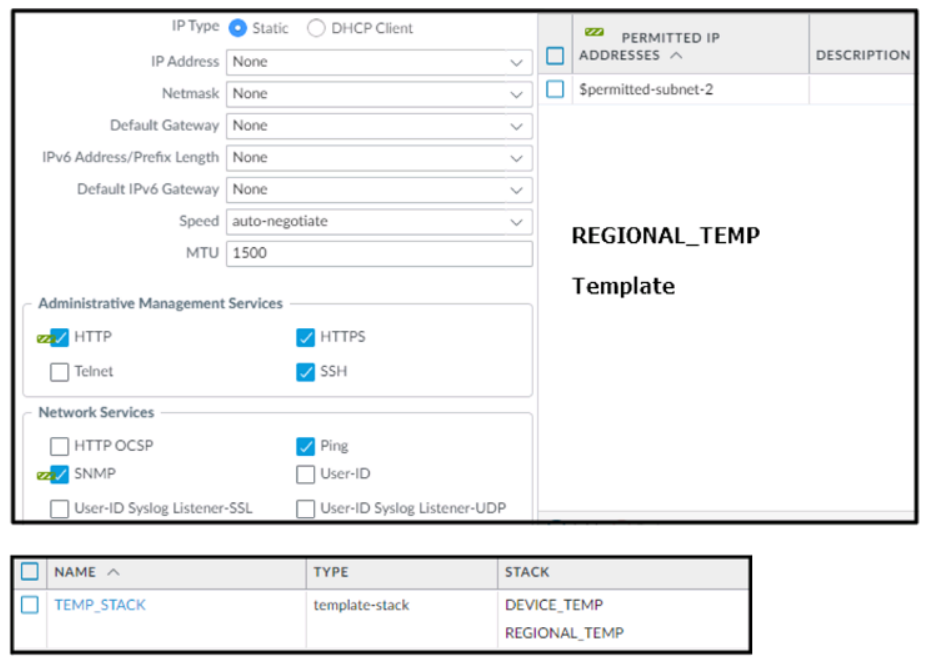
Based on the screenshots above, and with no configuration inside the Template Stack
itself, what access will the device permit on its Management port?
A. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1.
B. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-2.
C. The firewall will allow HTTP, Telnet, SNMP, HTTPS, SSH and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
D. The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
Explanation:
Key Observations from the Screenshot:
1.Administrative Management Services:
Enabled Services: HTTP, HTTPS, Telnet, SSH (explicitly listed).
Disabled Services: No mention of SNMP (though it appears under Network Services, it is not enabled for management access).
2.Permitted IP Addresses:
Only $permitted-subnet-2 is configured under PERMITTED IP ADDRESSES.
$permitted-subnet-1 is not listed, so it is not allowed.
3.Network Services:
Ping is enabled (under Network Services), but SNMP and others are separate from management access controls.
Why Not Other Options?
AIncorrectly includes $permitted-subnet-1, which is not configured.
CIncorrectly includes SNMP (not enabled for management) and $permitted-subnet-1.
DIncorrectly includes $permitted-subnet-1, which is absent.
Access Summary:
Allowed Protocols: HTTP, Telnet, HTTPS, SSH, Ping.
Permitted Source IPs: Only $permitted-subnet-2.
Reference:
Palo Alto Management Interface Documentation:
"Permitted IP addresses restrict management access to explicitly defined subnets."
Which CLI command displays the physical media that are connected to ethernet1/8?
A. > show system state filter-pretty sys.si. p8. stats
B. > show system state filter-pretty sys.sl.p8.phy
C. > show system state filter-pretty sys.sl.p8.med
D. > show interface ethernet1/8
Explanation:
The question asks for the CLI command that displays the physical media connected to ethernet1/8 on a Palo Alto Networks firewall. This requires identifying a command that provides detailed interface information, specifically related to the physical layer (e.g., media type, connection status). Let’s evaluate the options to determine the correct one.
Why > show system state filter-pretty sys.sl.p8.phy?
Purpose:
The show system state filter-pretty command is used to display detailed system state information in a human-readable format, filtered by specific parameters. The filter sys.sl.p8.phy targets the physical layer details of slot 1, port 8 (corresponding to ethernet1/8, where "p8" denotes port 8). This command provides information about the physical media, such as the type of cable or connection (e.g., copper, fiber) and its status.
Output:
The command will display details like the media type, link state, and speed/duplex settings for ethernet1/8. This is useful for troubleshooting physical connectivity issues.
Syntax Breakdown:
sys: System state.
sl: Slot (typically 1 for most firewalls, as ethernet1/8 is in slot 1).
p8: Port 8 (matching ethernet1/8).
phy: Physical layer information.
Reference:
Palo Alto Networks CLI Reference Guide indicates that show system state filter-pretty sys.sl.pX.phy is used to view physical media details for a specific port, where pX is the port number.
Why Not the Other Options?
A. > show system state filter-pretty sys.si.p8.stats:
Explanation:
The filter sys.si.p8.stats likely refers to interface statistics (e.g., packet counters) for port 8 in slot 1. While this provides performance data, it does not specifically display physical media details (e.g., cable type or connection status).
Why Incorrect: This command focuses on statistics, not physical media.
C. > show system state filter-pretty sys.sl.p8.med:
Explanation:
The filter sys.sl.p8.med appears to be a typo or incorrect syntax. There is no standard med parameter in the show system state command for physical media; the correct term is phy for physical layer details. This command would likely return no meaningful output or an error.
Why Incorrect: Invalid filter syntax makes this option non-functional.
D. > show interface ethernet1/8:
Explanation:
The show interface ethernet1/8 command displays operational status and configuration details for the specified interface, including IP address, speed, duplex, and link state. While it provides some physical layer information (e.g., link up/down), it is less detailed than the show system state filter-pretty sys.sl.p8.phy command for physical media specifics (e.g., media type).
Why Incorrect: This command is broader and less targeted to physical media details compared to the correct option.
Additional Context:
Interface Naming: On Palo Alto Networks firewalls, ethernet1/8 refers to slot 1, port 8. The CLI uses this notation to identify physical interfaces.
Troubleshooting Tip: To verify physical connectivity, use > show system state filter-pretty sys.sl.p8.phy alongside > show interface ethernet1/8 for a comprehensive view.
Best Practices:
Check cable type and compatibility (e.g., copper vs. fiber) using the physical media details.
Ensure the interface is administratively up (> configure; set interface ethernet1/8 enable yes).
PCNSE Exam Relevance: This question tests your knowledge of CLI commands for interface troubleshooting, a key skill in the PCNSE exam. It requires understanding the nuances of show system state filters.
Conclusion:
The CLI command that displays the physical media connected to ethernet1/8 is > show system state filter-pretty sys.sl.p8.phy, as it specifically targets the physical layer details for that port.
References:
Palo Alto Networks CLI Reference Guide: System State Commands
Palo Alto Networks Documentation: Interface Management
ExamTopics PCNSE Discussion: CLI Interface Commands
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports What can the engineer do to solve the VoIP traffic issue?
A. Disable ALG under H.323 application
B. Increase the TCP timeout under H.323 application
C. Increase the TCP timeout under SIP application
D. Disable ALG under SIP application
Explanation:
Why Disable SIP ALG?
1.The Problem:
The firewall is modifying SIP/H.323 payloads (e.g., NATing internal IPs/ports in VoIP packets).
This breaks VoIP signaling, as endpoints expect original headers for media negotiation.
2.The Cause:
SIP ALG (Application Layer Gateway) is enabled by default on NGFWs.
ALG inspects and rewrites SIP/H.323 packets, often misinterpreting VoIP traffic.
3.The Fix:
Disabling SIP ALG stops the firewall from:
Altering SIP packet payloads.
Opening incorrect dynamic pinholes for RTP/RTCP media streams.
Steps to Disable SIP ALG:
Navigate to: Device > Setup > Session
Under Application Identification, uncheck:
SIP (and optionally H.323 if used).
Why Not Other Options?
A.H.323 ALG is unrelated if SIP is the primary VoIP protocol.
B/C.Timeout adjustments don’t fix NAT-induced payload corruption.
Additional VoIP Best Practices:
Use dedicated SIP security profiles (e.g., allow only SIP/RTP/RTCP).
Ensure NAT policies exclude VoIP traffic (or use static NAT).
Reference:
Palo Alto VoIP Troubleshooting Guide:
"Disable SIP ALG when endpoints handle NAT traversal independently (e.g., via STUN/ICE)."
Following a review of firewall logs for traffic generated by malicious activity, how can an administrator confirm that WildFire has identified a virus?
A. By navigating to Monitor > Logs > WildFire Submissions, applying filter "(subtype eq wildfire-virus)"
B. By navigating to Monitor > Logs > Threat, applying filter "(subtype eq wildfire-virus)'
C. By navigating to Monitor > Logs > Traffic, applying filter "(subtype eq virus)"
D. By navigating to Monitor > Logs> Threat, applying filter "(subtype eq virus)"
Explanation:
To confirm that WildFire has identified a virus, the administrator must check the WildFire Submissions log. This log specifically tracks files submitted to WildFire and their verdicts.
The filter (subtype eq wildfire-virus) targets entries where WildFire has classified a file as malware (virus).
Threat logs (options B and D) show broader threat activity but do not confirm WildFire verdicts.
Traffic logs (option C) do not contain WildFire verdicts at all.
📘 Reference:
WildFire Log Review – Palo Alto Networks
PCNSE WildFire Log Filter Guide
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
A. SSH Service profile
B. SSL/TLS Service profile
C. Certificate profile
D. Decryption profile
Explanation:
Why SSL/TLS Service Profile?
1.Purpose:
The SSL/TLS Service Profile controls the cipher suites and protocols used for:
HTTPS management access (web interface).
API/CLI over TLS (e.g., Panorama communications).
2.Configuration:
Navigate to Device > Certificate Management > SSL/TLS Service Profile.
Specify allowed protocols (TLS 1.2/1.3) and custom cipher suites (e.g., AES256-GCM-SHA384).
Why Not Other Options?
A. SSH Service Profile
Only governs SSH ciphers (not HTTPS/API).
C. Certificate Profile
Defines trust for certificates, not cipher enforcement.
D. Decryption Profile
Used for traffic inspection, not management plane crypto.
Key Notes:
SSH Service Profile (Option A) is separate and controls SSH-specific ciphers (e.g., for CLI access).
Changes require commit and restart of management services.
Reference:
Palo Alto Admin Guide (SSL/TLS Profiles):
"SSL/TLS Service Profiles enforce cipher requirements for management interfaces."
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group. What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
A. A service route to the LDAP server
B. A Master Device
C. Authentication Portal
D. A User-ID agent on the LDAP server
1. Problem restatement
Engineer wants to use LDAP user groups in security rules (inside a Panorama Device Group).
For that, Panorama must know the mapping of users → groups.
Question: What must be configured so Panorama can retrieve user/group info?
2.Review the options
A. A service route to the LDAP server
Service routes define the source interface/IP for management-plane traffic (like LDAP queries, syslog, DNS, etc.).
Useful only if Panorama itself is talking to LDAP.
But Panorama does not retrieve group mappings directly — firewalls (User-ID) or Master Device handle it.
❌ Not the right answer.
B. A Master Device
✅ Correct.
In Panorama, if you want to use User-ID / group-based policies in a Device Group, you must designate a Master Device.
The Master Device is a firewall (in that Device Group) that retrieves group mapping from LDAP (via User-ID or User-ID agent).
Panorama then uses that device’s mappings to show groups for policy creation.
C. Authentication Portal ❌
Auth portal (Captive Portal) is for authenticating unknown users (BYOD, guest, etc.).
Doesn’t solve LDAP group lookup in Panorama.
D. A User-ID agent on the LDAP server ❌
You can run a User-ID agent on Windows or use the firewall’s built-in User-ID.
That’s how group mappings get retrieved.
But for Panorama Device Groups, you still need to configure a Master Device to pull those mappings.
📖 Reference
Palo Alto Networks Admin Guide – “To enable group-based policy in Panorama-managed firewalls, you must configure a Master Device. The Master Device provides the group mappings (retrieved from LDAP through User-ID) to Panorama so that you can reference user groups in policies.”
A decryption policy has been created with an action of "No Decryption." The decryption profile is configured in alignment to best practices. What protections does this policy provide to the enterprise?
A. It allows for complete visibility into certificate data, ensuring secure connections to all websites.
B. It ensures that the firewall checks its certificate store, enabling sessions with trusted self-signed certificates even when an alternative trust anchor exists.
C. It encrypts all certificate information to maintain privacy and compliance with local regulations.
D. It enhances security by actively blocking access to potentially insecure sites with expired certificates or untrusted issuers.
Explanation:
The scenario involves a decryption policy with an action set to "No Decryption," paired with a decryption profile configured according to best practices on a Palo Alto Networks firewall. The question asks what protections this policy provides to the enterprise. Let’s analyze the configuration and evaluate the options.
Configuration Context:
Decryption Policy with "No Decryption": This action indicates that the firewall will not decrypt the SSL/TLS traffic matching this policy. Instead, it will allow the traffic to pass through without inspection of the encrypted payload. However, the firewall still evaluates the SSL/TLS handshake and certificate details against the associated decryption profile.
Decryption Profile: A decryption profile defines rules for handling SSL/TLS sessions, such as certificate validation, supported protocols, and ciphers. Best practices for a decryption profile typically include:
Enforcing strict certificate validation (e.g., checking for expired certificates, untrusted issuers, or revoked certificates via CRL/OCSP).
Blocking sessions that fail these checks.
Limiting supported TLS versions and ciphers to enhance security.
Impact: Even with "No Decryption," the firewall can still provide security by enforcing certificate-based controls defined in the decryption profile, rather than allowing all traffic blindly.
Why D. It enhances security by actively blocking access to potentially insecure sites with expired certificates or untrusted issuers?
Purpose:When the decryption action is set to "No Decryption," the firewall does not decrypt the traffic but still inspects the SSL/TLS handshake. The decryption profile, configured to best practices, includes rules to validate certificates. If a certificate is expired, issued by an untrusted Certificate Authority (CA), or otherwise invalid, the firewall can block the session based on the profile’s settings (e.g., "Block" action for failed certificate checks).
Protection Mechanism:
The profile checks the certificate chain, expiration dates, and trust status against the firewall’s trusted CA list.
If the certificate fails validation, the session is blocked, preventing access to insecure or potentially malicious sites.
Best Practice Alignment: A well-configured decryption profile includes options like "Block sessions with expired certificates" and "Block sessions with untrusted issuers," which are active even with "No Decryption."
Reference: Palo Alto Networks documentation states, "Even with No Decryption, the firewall can enforce certificate validation rules from the decryption profile to block insecure connections."
Why Not the Other Options?
A. It allows for complete visibility into certificate data, ensuring secure connections to all websites:
Explanation: "No Decryption" means the firewall does not inspect the encrypted payload or provide visibility into the content of the traffic. While it can see certificate data during the handshake, it does not ensure secure connections to all websites; it only blocks insecure ones based on certificate validation.
Why Incorrect: This overstates the visibility and security assurance, as decryption is not performed.
B. It ensures that the firewall checks its certificate store, enabling sessions with trusted self-signed certificates even when an alternative trust anchor exists:
Explanation: The firewall checks certificates against its trusted CA store, but "No Decryption" does not inherently allow sessions with self-signed certificates unless they are explicitly trusted (added to the firewall’s certificate store). If an alternative trust anchor exists and is untrusted, the session would be blocked, not enabled.
Why Incorrect: This misrepresents the behavior; self-signed certificates are blocked unless pre-trusted, and the focus is on blocking, not enabling.
C. It encrypts all certificate information to maintain privacy and compliance with local regulations:
Explanation: "No Decryption" does not encrypt certificate information; the certificates are already encrypted in the SSL/TLS handshake and visible to the firewall during validation. The policy does not alter or encrypt data; it passes traffic without inspection.
Why Incorrect: This is factually incorrect, as the policy does not perform encryption.
Additional Context:
Decryption Policy Types: Options include "Decrypt" (full inspection), "No Decryption" (pass-through with validation), and "Decrypt & Forward Proxy" (for outbound traffic). "No Decryption" is often used for traffic where decryption is impractical (e.g., performance constraints) but still requires security checks.
Best Practice Configuration:
Enable "Block sessions with expired certificates" and "Block sessions with untrusted issuers" in the decryption profile.
Use a Forward Trust certificate or external CA for trusted sites.
Exclude high-risk traffic from decryption only after validating certificates.
Monitoring:
Check Monitor > Logs > Threat for blocked sessions due to certificate issues.
PCNSE Exam Relevance: This question tests your understanding of decryption policies and profiles, a key topic in the PCNSE exam. It requires knowledge of how "No Decryption" interacts with certificate validation.
Conclusion:
A decryption policy with an action of "No Decryption" and a best-practices decryption profile enhances security by actively blocking access to potentially insecure sites with expired certificates or untrusted issuers, leveraging certificate validation without decrypting the traffic.
References:
Palo Alto Networks Documentation: Decryption Policy Configuration
Palo Alto Networks Documentation: Decryption Profile Best Practices
ExamTopics PCNSE Discussion: Decryption and Certificate Validation
| Page 4 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home | Previous |