Why would a traffic log list an application as "not-applicable”?
A. The firewall denied the traffic before the application match could be performed.
B. The TCP connection terminated without identifying any application data
C. There was not enough application data after the TCP connection was established
D. The application is not a known Palo Alto Networks App-ID.
Explanation:
The key to understanding this lies in the Palo Alto Networks firewall's policy evaluation order, specifically the relationship between rules that block traffic and the App-ID process.
App-ID is a powerful feature, but it does not happen first. The firewall processes traffic in a specific sequence. If a security rule with a Deny action matches the traffic based on earlier criteria (like Source/Destination Zone, Address, or User), the session is immediately dropped. The firewall does not invest resources in performing deep packet inspection (App-ID) on traffic it has already decided to block.
When this happens, the Traffic log will show the Application as not-applicable because the application was never identified.
Why the other options are incorrect:
B. The TCP connection terminated without identifying any application data and C.
There was not enough application data after the TCP connection was established: These scenarios are related to the App-ID process itself. In these cases, the firewall attempted to identify the application but could not. This would typically result in the application being labeled as incomplete or falling back to a base protocol (like ssl or tcp), not not-applicable.
D. The application is not a known Palo Alto Networks App-ID:
If the firewall processes the traffic (allows it through a rule) and successfully identifies it as an unknown application, it will be classified under the unknown application or, more commonly, unknown-tcp or unknown-udp. Again, this is different from not-applicable.
🔍 Reference:
Palo Alto Networks – Traffic Log Fields
Palo Alto Knowledge Base – Why Application is 'not-applicable'
An engineer is tasked with deploying SSL Forward Proxy decryption for their organization. What should they review with their leadership before implementation?
A. Browser-supported cipher documentation
B. Cipher documentation supported by the endpoint operating system
C. URL risk-based category distinctions
D. Legal compliance regulations and acceptable usage policies
Explanation:
Deploying SSL Forward Proxy (Decryption) is a powerful security measure, but it also has significant legal and privacy implications. The firewall will essentially act as a "Man-in-the-Middle" (MiTM), terminating and inspecting encrypted traffic that users believe is private between their browser and the website.
Before implementing such a technology, it is absolutely critical to review this with leadership and legal counsel for the following reasons:
Legal Compliance: Many regions and countries have strict data privacy laws (such as GDPR, CCPA, etc.) that govern the monitoring of user communications. Intercepting user traffic, even for security purposes, may be restricted or require specific disclosures.
Acceptable Use Policy (AUP): The organization's AUP must explicitly state that network traffic, including encrypted traffic, is subject to monitoring for security and compliance purposes. Employees should be made aware of this practice. Without a clear AUP, decryption could lead to legal challenges from employees.
User Notification: Leadership must decide on a policy for user notification. While often not legally required to obtain individual consent in a corporate environment, it is a best practice to inform users that their traffic is being decrypted and inspected.
Reviewing these points with leadership ensures the deployment is not only technically sound but also legally defensible and aligned with the organization's ethical standards.
Why the other options are incorrect:
A. Browser-supported cipher documentation & B. Cipher documentation supported by the endpoint operating system:
These are important technical considerations for the engineer. They need to ensure the firewall uses ciphers that the clients (browsers and OS) support to avoid breaking legitimate applications. However, these are implementation details that do not require leadership review.
C. URL risk-based category distinctions:
This is a configuration detail for the Decryption policy. An engineer would use URL categories to decide which traffic to decrypt (e.g., decrypt "Financial Services" but not "Healthcare"). This is a technical and policy-configuration decision, not a high-level leadership discussion about legality and user privacy.
Reference:
The Palo Alto Networks Decryption Administrator's Guide and the PCNSE study materials heavily emphasize the legal and privacy considerations as a primary step before deploying decryption. It is a foundational best practice to get organizational buy-in and ensure compliance with local laws.
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two.)
A. ECDSA
B. ECDHE
C. RSA
D. DHE
Explanation:
The resource consumption during SSL/TLS decryption is primarily driven by the key exchange process. The firewall, acting as a SSL Forward Proxy, must perform the cryptographic computations for both the client and server sides of the connection.
The key differentiator is whether the key exchange uses Ephemeral keys. Ephemeral key exchange methods generate a temporary, unique key for each session, which provides Perfect Forward Secrecy (PFS). This enhanced security comes at the cost of significantly higher computational overhead.
D. DHE (Diffie-Hellman Ephemeral):
This is the classic ephemeral key exchange algorithm. It is very computationally intensive for both the client and the server (in this case, the firewall performing decryption) because it involves complex modular exponentiation calculations for every single new session.
B. ECDHE (Elliptic Curve Diffie-Hellman Ephemeral):
This is the elliptic curve variant of DHE. While ECDHE is more efficient than DHE for the same level of security (it uses smaller key sizes), it is still significantly more resource-intensive than non-ephemeral methods like RSA. The elliptic curve operations, though efficient, must still be performed for every new session, leading to high CPU consumption on the firewall when decrypting a large volume of connections.
Why the other options are incorrect:
A. ECDSA (Elliptic Curve Digital Signature Algorithm):
This is used for authentication (proving the server's identity), not for key exchange. While it does use CPU cycles, its impact is minor compared to the ongoing overhead of ephemeral key exchange algorithms. The question specifically asks about the key exchange process.
C. RSA:
In a key exchange context, RSA is a non-ephemeral method. The server's static RSA private key is used to encrypt the pre-master secret. This operation is computationally expensive, but it is only performed once per session during the handshake and is generally less CPU-intensive than the sustained calculations required by DHE and ECDHE, especially at scale. Modern firewalls often have hardware acceleration for RSA operations.
Reference:
Palo Alto Networks documentation and whitepapers on decryption performance consistently highlight that enabling Perfect Forward Secrecy (PFS), which uses ephemeral key exchanges like DHE and ECDHE, will increase the firewall's CPU utilization and reduce the maximum decryption throughput compared to using non-ephemeral methods like RSA key exchange.
An auditor is evaluating the configuration of Panorama and notices a discrepancy between the Panorama template and the local firewall configuration. When overriding the firewall configuration pushed from Panorama, what should you consider?
A. The firewall template will show that it is out of sync within Panorama.
B. The modification will not be visible in Panorama.
C. Only Panorama can revert the override.
D. Panorama will update the template with the overridden value.
Detailed Explanation:
When a local override is applied on a firewall (modifying a Panorama-pushed configuration):
B. The modification will not be visible in Panorama.
Panorama does not automatically detect or display locally overridden values on the firewall.
The firewall retains its local changes, but Panorama still shows its original template configuration.
Why the Other Options Are Incorrect:
A. Panorama does not automatically flag templates as "out of sync" due to local overrides (manual review is required).
C. Both Panorama and the firewall CLI can revert overrides (Panorama is not the only method).
D. Panorama does not auto-update templates with locally overridden values (changes must be manually pushed from Panorama).
Best Practice:
Use "Force Template Values" in Panorama to eliminate local overrides and enforce centralized management.
Reference:
Panorama Local Overrides Documentation
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
A. A Deny policy for the tagged traffic
B. An Allow policy for the initial traffic
C. A Decryption policy to decrypt the traffic and see the tag
D. A Deny policy with the "tag" App-ID to block the tagged traffic
Explanation:
Dynamic User Groups (DUGs) in Palo Alto Networks firewalls are used to dynamically assign users to groups based on tags pushed from external systems like Cortex XSOAR, XDR, or via the XML API. These allow for real-time enforcement of security policies without requiring user logout/login or group refreshes.
To block traffic in real time using DUGs, the following policy components are needed:
🔹 A. A Deny policy for the tagged traffic
This is the actual policy that references the Dynamic User Group and blocks traffic for users dynamically added to the group.
Once a user is tagged (e.g., as "malicious" or "violator"), this rule becomes effective immediately, blocking their access based on the DUG membership.
🔹 B. An Allow policy for the initial traffic
Before the user is tagged and added to the DUG, they still need to be allowed to generate traffic so they can be evaluated or monitored.
This initial allow policy ensures the traffic is visible and can be tagged (e.g., by a monitoring or detection system like Cortex XDR).
❌ Why the other options are incorrect:
C. A Decryption policy to decrypt the traffic and see the tag:
Tags and DUG membership are independent of traffic decryption. DUG enforcement is based on user identity and tag, not packet content.
D. A Deny policy with the "tag" App-ID to block the tagged traffic:
Tags are not App-IDs. A tag is an identifier for grouping users in DUGs, not an application signature. So there is no "tag" App-ID.
🔍 Reference:
Palo Alto Networks – Dynamic User Groups:
Dynamic User Groups (DUGs) Overview
Best Practices for DUG Implementation:
Palo Alto Live Community – Using Dynamic User Groups to Quarantine Users
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
A. HTTPS
B. SSH
C. Permitted IP Addresses
D. HTTP
E. User-IO
Explanation:
When allowing management access on an external-facing interface (like untrust), it is critical to limit the exposure to reduce the attack surface. The Interface Management Profile is the primary tool for this, controlling how and from where the firewall can be managed.
A. HTTPS & B. SSH:
These are the secure protocols you would enable to allow the remote administrator to actually access the firewall's WebUI (HTTPS) and Command Line Interface (SSH). You should disable insecure protocols like HTTP and Telnet.
C. Permitted IP Addresses:
This is the most crucial security control. Instead of allowing management access from any IP address on the internet, this setting restricts access to only the specific, known IP address (or range) from which the administrator will be connecting. This dramatically reduces the attack surface, preventing random scanners and attackers from even reaching the login prompts for HTTPS or SSH.
Why the other options are incorrect:
D. HTTP:
This is an insecure protocol that transmits credentials and data in plaintext. It should never be enabled for management access, especially on an untrust interface. Enabling HTTP would be a severe security misconfiguration.
E. User-IO:
This service is related to the firewall's physical console port access. It is used for out-of-band management when you are physically connected to the device with a keyboard and monitor. It is completely irrelevant for securing remote network-based management access over the untrust interface.
Best Practices:
Always disable HTTP and Ping on untrust interfaces.
Use certificate-based authentication for HTTPS/SSH if possible.
Reference:
Palo Alto Interface Management Profile Docs
Exhibit.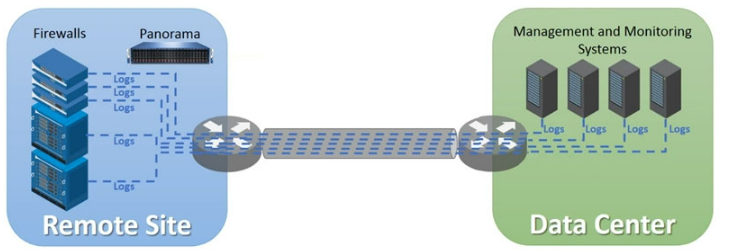
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and
security management platforms The network team has reported excessive traffic on the
corporate WAN How could the Palo Alto Networks NGFW administrator reduce WAN traffic
while maintaining support for all the existing monitoring/security platforms?
A. Any configuration on an M-500 would address the insufficient bandwidth concerns
B. Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW
C. Configure log compression and optimization features on all remote firewalls
D. Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services
Explanation:
In the image, we see multiple firewalls at a remote site sending logs directly to both Panorama and to various management and monitoring systems at the data center, which consumes significant WAN bandwidth.
To reduce WAN traffic while maintaining the existing log visibility:
🔄 Centralize log forwarding:
Send logs only once across the WAN — from the firewalls to Panorama — and let Panorama handle the log forwarding to all other systems (SIEM, monitoring tools, etc.).
This drastically cuts down on duplicate log traffic over the WAN.
🔍 Why the other options are incorrect:
A. Any configuration on an M-500 would address the insufficient bandwidth concerns:
❌ Incorrect. The M-500 is a Panorama appliance, and its configuration affects log storage/management but doesn't inherently reduce WAN bandwidth unless used properly in architecture like option D.
B. Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW:
❌ Reversed logic. Logs go from NGFWs to Panorama, not the other way around.
C. Configure log compression and optimization features on all remote firewalls:
❌ PAN-OS does not support log compression across WAN links for remote log forwarding. So this option is not feasible.
🧠 Best Practice:
Use Panorama in "Log Collector mode" or dedicated log collectors to centralize logs.
Use Panorama’s Log Forwarding feature to relay logs to external monitoring and SIEM systems.
This keeps only one copy of each log traveling across the WAN, minimizing traffic and duplication.
📚 Reference:
Palo Alto Networks – Log Forwarding
Palo Alto Networks – Best Practices for Distributed Log Collection
Refer to the exhibit.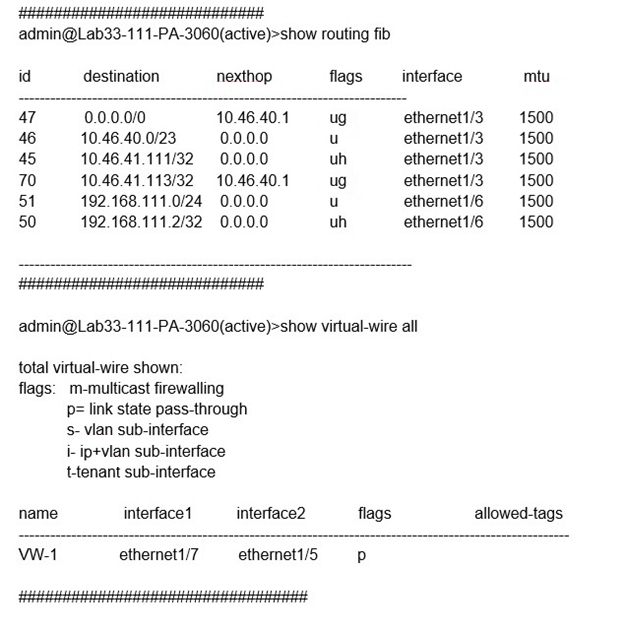
Which will be the egress interface if the traffic's ingress interface is ethernet1/7 sourcing
from 192.168.111.3 and to the destination 10.46.41.113?
A. ethernet1/6
B. ethernet1/3
C. ethernet1/7
D. ethernet1/5
Explanation:
1. Understanding the Traffic Flow
Ingress Interface: ethernet1/7 (Virtual Wire member, as seen in show virtual-wire all).
Source IP: 192.168.111.3 (part of subnet 192.168.111.0/24, locally attached to ethernet1/6).
Destination IP: 10.46.41.113 (routed via 10.46.40.1 on ethernet1/3, per the FIB table).
2. Virtual Wire Behavior
The show virtual-wire all output shows:
VW-1 binds ethernet1/7 (ingress) to ethernet1/5 (egress).
Flags: p (link state pass-through), meaning traffic bypasses Layer 3 routing.
Critical Point: Virtual Wire interfaces forward traffic directly between paired interfaces without routing.
3. Why Not Other Options?
A. ethernet1/6 → Incorrect. This is the L3 interface for 192.168.111.0/24, but traffic enters via Virtual Wire (ethernet1/7).
B. ethernet1/3 → Incorrect. This is the L3 egress for 10.46.41.113, but Virtual Wire bypasses routing.
C. ethernet1/7 → Incorrect. This is the ingress interface, not egress.
4. Key Takeaway
Virtual Wire (transparent mode) forwards traffic at Layer 2 between paired interfaces. Since ethernet1/7 is paired with ethernet1/5, traffic exits via ethernet1/5.
Reference:
Palo Alto Admin Guide (Virtual Wire):
Virtual Wire interfaces do not participate in routing; traffic flows directly between paired interfaces.
| Page 2 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home |