The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
A. Management plane CPU
B. Dataplane CPU
C. Packet buffers
D. On-chip packet descriptors
Explanation:
In a Palo Alto Networks firewall, different planes handle different responsibilities:
Dataplane (DP):
Handles traffic processing (App-ID, Content-ID, session handling, encryption, etc.).
Uses dedicated CPUs (network processors, security processors).
Optimized for packet flow, not log forwarding.
Management plane (MP):
Handles management tasks like GUI/CLI, configuration commits, and log processing & log forwarding.
Whenever logs need to be sent to Panorama, SIEM, or external log collectors, this is done by the management plane CPU.
Packet buffers:
Buffers used in the dataplane for temporary packet storage.
If overutilized, you see packet drops — but unrelated to log forwarding.
On-chip packet descriptors:
Hardware structures in the dataplane to describe packets in processing pipelines.
Again, related to traffic handling, not log forwarding.
👉 Therefore, the correct component responsible for log forwarding is the Management Plane CPU.
If the firewall is forwarding a large volume of logs to Panorama, you should monitor MP CPU utilization for early signs of overloading.
Reference:
Palo Alto Networks TechDocs: Firewall Architecture Overview
PAN KB: Which plane processes what?
A company has configured GlobalProtect to allow their users to work from home. A decrease in performance for remote workers has been reported during peak-use hours. Which two steps are likely to mitigate the issue? (Choose TWO)
A. Exclude video traffic
B. Enable decryption
C. Block traffic that is not work-related
D. Create a Tunnel Inspection policy
Explanation:
When remote users connect via GlobalProtect, all their traffic is routed through the VPN tunnel. During peak hours, this can overwhelm bandwidth and processing capacity. The goal is to reduce unnecessary traffic and prioritize business-critical flows.
A. Exclude video traffic — ✅ Correct
Video streaming (e.g., YouTube, Netflix, Zoom background video) consumes massive bandwidth.
You can configure split tunneling to exclude such traffic from the VPN tunnel.
This allows video traffic to go directly to the internet, bypassing the firewall.
📚 Reference:
Palo Alto Networks – Configure Split Tunneling for GlobalProtect
C. Block traffic that is not work-related — ✅ Correct
Use Security Policies and App-ID to block social media, gaming, and other non-business apps.
Reduces load on the VPN and ensures bandwidth is reserved for work-related traffic.
📚 Reference:
Palo Alto Networks – Use App-ID to Control Applications
❌ Incorrect Options:
B. Enable decryption:
This increases CPU load and latency. It’s useful for visibility, but not a performance optimization.
D. Create a Tunnel Inspection policy:
Tunnel Inspection is for analyzing IPSec/GRE tunnels — not relevant to GlobalProtect performance.
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A. DNS Proxy
B. SSL/TLS profiles
C. address groups
D. URL Filtering profiles
Explanation:
To understand why, you must remember the core principle of the Panorama Device Group structure: its purpose is to push shared policy and object configurations to a group of firewalls. The key is knowing which configurations are universal (shared) and which are specific to a firewall's placement in the network (unique).
Device Groups are used for policies and objects that can be shared across multiple firewalls. Let's break down the correct answers:
C. address groups
Why it's configurable: Address groups (and other object types like address objects, service objects, and service groups) are abstract definitions (e.g., "Finance-Servers" = 10.10.10.0/24). These definitions are perfectly reusable across many firewalls. By configuring them in a Device Group, you ensure consistency and simplify policy management for all firewalls in that group.
D. URL Filtering profiles
Why it's configurable: Security profiles (URL Filtering, Anti-Virus, Vulnerability Protection, etc.) are policy building blocks. You can define a "Standard-Web-Policy" profile in a Device Group and then reference that same profile in the Security policies of all member firewalls. This ensures a uniform security posture across the organization.
Detailed Analysis of the Incorrect Options:
A. DNS Proxy
Why it's NOT configurable: DNS Proxy is a network service that must be bound to a specific VLAN or interface on a firewall. Since each firewall has unique interfaces and network placements, this configuration cannot be shared across a group of devices. This type of network configuration is pushed from Templates, not Device Groups.
B. SSL/TLS profiles
Why it's NOT configurable (in this context): This is a subtle but important distinction. While you can create an SSL/TLS Service Profile (which contains the certificates and trust settings) in a Device Group, you cannot apply it to an interface or service there. The application of the profile (e.g., assigning it to a Decryption policy) is done in a Device Group, but the core profile configuration that includes interface-specific settings is a Template-level function. More importantly, the actual decryption rules that use the profile are configured in the Device Group. However, given the option list and the standard PCNSE curriculum, this is not considered a primary "object" for a Device Group in the same way as Address Groups or Security Profiles. The safest answer is that it's primarily a Template/Network function.
PCNSE Exam Reference & Key Takeaway:
Core Concept: The separation of duties between Device Groups and Templates in Panorama.
Device Groups: For policies and shared objects (Security, NAT, Decryption Policies, Address Groups, Service Groups, Security Profiles).
Templates: For network configuration (Interfaces, Zones, Virtual Routers, VLANs, DNS Proxy, DHCP Server, SSL/TLS Service Profiles for inbound decryption).
Simplified Rule of Thumb: If the configuration answers "What is the rule?" or "What is the security setting?", it goes in a Device Group. If it answers "Where is the firewall connected?" or "How is a network service provided?", it goes in a Template.
An engineer is configuring a Protection profile to defend specific endpoints and resources
against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for
specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
A. Packet Buffer Protection
B. Zone Protection
C. Vulnerability Protection
D. DoS Protection
Explanation:
There are several protection mechanisms in PAN-OS:
1.Zone Protection Profile
Applied per zone (ingress).
Provides broad flood protection (SYN floods, ICMP floods, UDP floods, reconnaissance protection, etc.).
It’s not granular to specific hosts — it protects the entire zone.
❌ Not the right answer here, because the question asks about specific critical systems.
DoS Protection Profile ✅
Applied per policy rule, which can match specific IPs, subnets, or services.
Provides granular flood protection for critical resources.
Can protect specific servers/endpoints against SYN/ICMP/UDP floods.
Exactly matches the requirement in the question: “granular defense against targeted flood attacks for specific critical systems accessed from the internet.”
3.Packet Buffer Protection
Protects the firewall itself from resource exhaustion (buffer overflows in the dataplane).
It is not about defending endpoints or servers.
4.Vulnerability Protection
Provides defense against exploits (e.g., buffer overflow attempts, protocol anomalies, exploit kits).
Works at the application/content layer.
Not for flood protection.
Why D is Correct:
The engineer wants to protect specific critical endpoints against flood attacks → That’s exactly what DoS Protection Profiles are for.
Reference:
Palo Alto Networks TechDocs: DoS Protection Profiles
Palo Alto Networks: Difference between Zone Protection and DoS Protection
Review the information below. A firewall engineer creates a U-NAT rule to allow users in
the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as
expected?
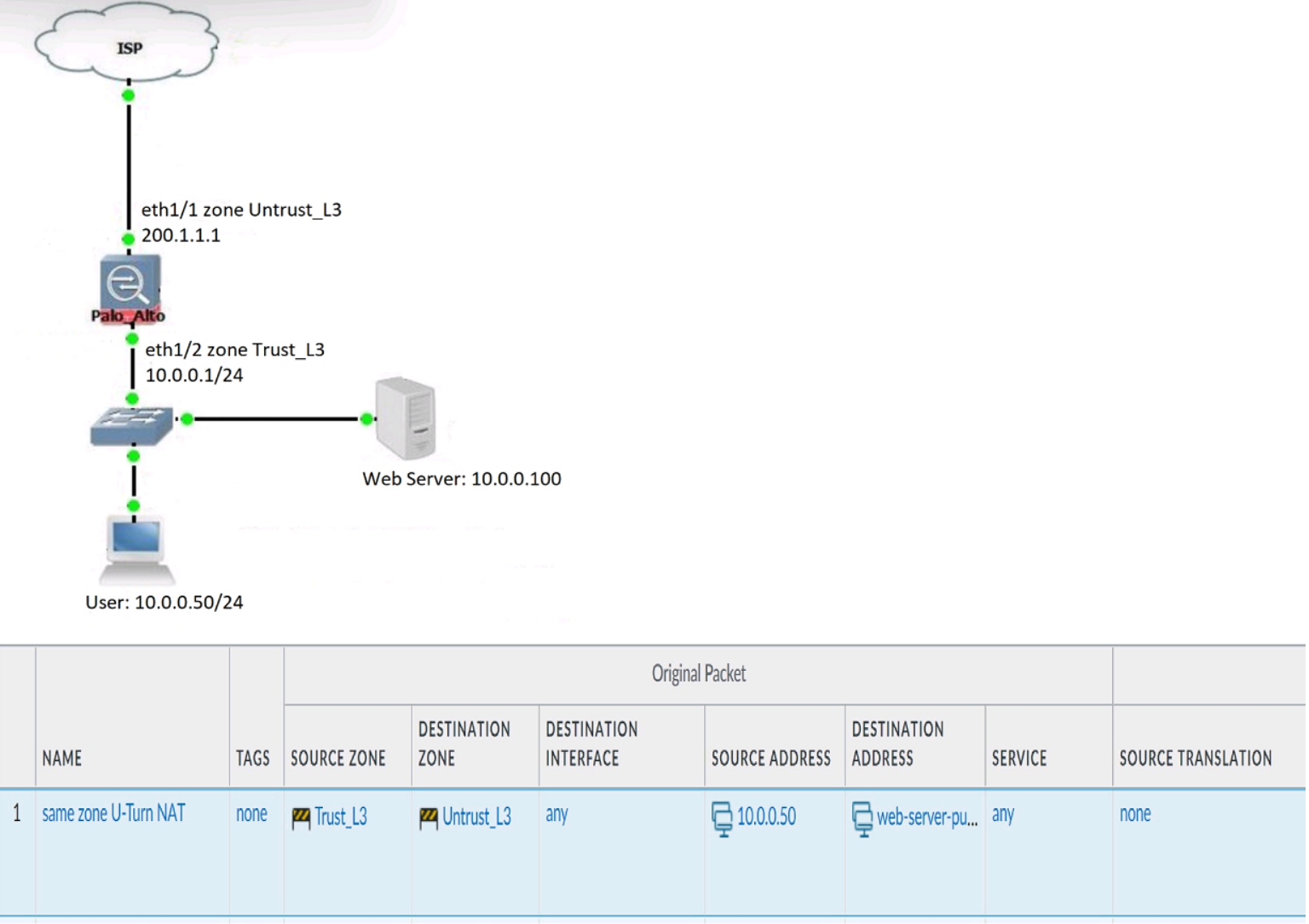
A. Change destination NAT zone to Trust_L3.
B. Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
C. Change Source NAT zone to Untrust_L3.
D. Add source Translation to translate original source IP to the firewall eth1/2 interface translation.
Explanation:
This is a classic U-Turn NAT scenario, where internal users access an internal server using its public IP address. For this to work correctly, the NAT rule must reflect that both source and destination traffic are in the same zone — in this case, Trust_L3.
Why A is Correct:
The destination zone in the NAT rule must match the zone of the translated IP (i.e., the internal server).
Since the public IP is translated to 10.0.0.100, which resides in Trust_L3, the destination zone must be Trust_L3.
If you leave it as Untrust_L3, the firewall won’t match the NAT rule correctly, and the traffic will fail.
📚 Reference:
Palo Alto Networks – U-Turn NAT Configuration
❌ Why Other Options Are Wrong:
B. Dynamic IP translation:
Not relevant — this is a destination NAT scenario, not source NAT.
C. Source NAT zone to Untrust_L3:
Incorrect — the source zone is Trust_L3 and should remain so.
D. Add source translation:
Not required for U-Turn NAT unless there's a specific need to mask internal IPs.
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet. Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
A. Post-NAT source IP address Pre-NAT source zone
B. Post-NAT source IP address Post-NAT source zone
C. Pre-NAT source IP address Post-NAT source zone
D. Pre-NAT source IP address Pre-NAT source zone
Explanation:
QoS rules are evaluated before NAT is applied (similar to security policies).
This means:
You must use the original (pre-NAT) IP address of the server.
You must also use the pre-NAT zone (the ingress zone where the traffic arrives).
Why pre-NAT?
NAT happens later in the processing sequence (after policy lookup).
QoS, like security rules, must decide based on the original values (source/destination IP + zones) before NAT rewrites them.
Why the other options are incorrect:
A. Post-NAT source IP + Pre-NAT zone ❌
Mixing pre- and post-NAT info doesn’t work.
B. Post-NAT source IP + Post-NAT source zone ❌
Incorrect because QoS doesn’t use post-NAT information for rule matching.
C. Pre-NAT source IP + Post-NAT source zone ❌
Again mixing pre- and post-NAT fields. Invalid.
D. Pre-NAT source IP + Pre-NAT source zone ✅
Correct, because QoS policy rules use pre-NAT source/destination addresses and zones.
Reference:
Palo Alto Networks TechDocs: QoS Policy Rules
PAN KB: Understanding Pre-NAT vs Post-NAT Policy Matching
A company configures its WildFire analysis profile to forward any file type to the WildFire public cloud. A company employee receives an email containing an unknown link that downloads a malicious Portable Executable (PE) file. What does Advanced WildFire do when the link is clicked?
A. Performs malicious content analysis on the linked page, but not the corresponding PE file.
B. Performs malicious content analysis on the linked page and the corresponding PE file.
C. Does not perform malicious content analysis on either the linked page or the corresponding PE file.
D. Does not perform malicious content analysis on the linked page, but performs it on the corresponding PE file.
Explanation:
Advanced WildFire provides multi-stage analysis for both web content and downloaded files. When a user clicks a suspicious link, WildFire can:
Analyze the linked page for:
Embedded scripts
Redirects
Exploit kits
Malicious behaviors
Analyze the downloaded file (in this case, a Portable Executable) for:
Behavioral indicators in a sandbox
Static and dynamic analysis
Malware signatures
Because the WildFire profile is configured to forward any file type, and the firewall detects both the URL and the downloaded PE file, both are submitted for analysis.
📚 Reference:
Palo Alto Networks – WildFire Analysis Workflow
❌ Why Other Options Are Wrong:
A. Incorrect — WildFire does analyze the PE file.
C. Incorrect — WildFire analyzes both components if properly configured.
D. Incorrect — WildFire does analyze the linked page if it’s suspicious.
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A. Custom URL category in URL Filtering profile
B. EDL in URL Filtering profile
C. PAN-DB URL category in URL Filtering profile
D. Custom URL category in Security policy rule
Explanation:
To determine the processing order, you must understand the hierarchy of policy enforcement on a Palo Alto Networks firewall. The system evaluates different components in a strict sequence, and a traffic flow must pass through all of them to be allowed.
The relevant order for this question is:
URL Filtering Profile (PAN-DB & EDL): The firewall first checks the URL against the URL Filtering profile attached to the matching Security policy. Within the profile, it evaluates the URL against its configured settings in a specific internal order.
Security Policy Rule (Custom URL Category): Only after the traffic has been evaluated and allowed by the URL Filtering profile does it proceed to be evaluated by the Security policy rule again for the final permit/deny decision. The custom URL category applied directly to the Security policy rule is part of this final check.
Let's break down why D is evaluated last:
A, B. and C are all components of a URL Filtering Profile. The firewall processes the URL Filtering profile as a single step. It checks the requested URL against the PAN-DB category (C), any External Dynamic Lists (EDLs) (B), and any custom URL categories (A) defined within that profile. The result of this entire profile evaluation (allow, block, alert, continue) is determined here. If the profile is set to block based on any of these three internal components (A, B, or C), the traffic is dropped immediately and never reaches the final Security Policy rule evaluation.
D .is part of the Security Policy Rule. A custom URL category can be added as a matching criterion directly in a Security policy rule. For the firewall to even consider this criterion, the traffic must have first been allowed by the URL Filtering profile. If the traffic was not blocked by the profile, it then moves to the final step: the Security policy rule check. Here, if the URL matches the custom category and the rule's action is set to deny, it will be blocked at this final stage.
Therefore, a block action triggered by a custom URL category in the Security policy rule (D) occurs after the traffic has successfully passed through (was allowed by) the URL Filtering profile.
Detailed Analysis of the Processing Order:
URL Filtering Profile Evaluation: The URL is checked.
Is it in a PAN-DB category set to block? (C) -> Blocked HERE.
Is it on an EDL set to block? (B) -> Blocked HERE.
Is it in a custom category within the profile set to block? (A) -> Blocked HERE.
If none of the above trigger a block, the profile allows the traffic to continue to the next step.
Security Policy Rule Evaluation: The traffic, now allowed by the URL Filtering profile, is evaluated against the Security policy rule.
Does the URL match the custom URL category defined in this rule? (D)
If yes, and the action is deny -> Blocked HERE (LAST).
PCNSE Exam Reference & Key Takeaway:
Core Concept: Policy Evaluation Order. A key mantra is "Profiles before Policy." Security profiles (URL Filtering, Vulnerability, Anti-Virus, etc.) are evaluated before the final allow/deny action of the Security policy rule is executed.
Troubleshooting: If a URL is being blocked and you can't figure out why, check the Traffic logs. The logs will clearly show the distinct phases:
A log-end reason of "url-block" indicates it was blocked by the URL Filtering profile (A, B, or C).
A log-end reason of "deny" indicates it was matched and blocked by the Security policy rule itself (D).
Use Case:
Placing a block in the Security policy (D) is useful for creating very explicit, high-priority deny rules that you want to be visible directly in the policy list. However, most URL blocking is efficiently handled within the URL Filtering profile.
| Page 11 out of 41 Pages |
| Palo Alto PCNSE Practice Test Home | Previous |